This Week on The Awareness Angle -
- Google’s own safety tools are being used to wipe people’s phones.
- A Chinese state group ran an AI driven espionage campaign with almost no humans involved.
- And a two billion record credential dump reminds us that password reuse is still one of the biggest risks out there.
This week’s episode looks at what happens when everyday tools become attack surfaces. From cloud accounts acting like remote kill switches to AI agents running full intrusion chains, Ant and Luke break down the human choices, habits and gaps that make these attacks possible.
Also this week, Checkout dot com turns an extortion attempt into a win for the industry, Norway discovers its buses can be remotely stopped, and a new phishing kit shows how criminal tools are becoming as slick as the legit ones.
🎧 Listen on your favourite podcast platform - Spotify, Apple Podcasts and YouTube

Listen Now
Podcast · Risky CreativeThis week's stories...
Checkout dot com stands up to extortion
This one deserves the spotlight because it is rare to see a company take an attack and turn it into something genuinely positive. ShinyHunters tried to extort Checkout dot com after accessing an old third-party storage system that should have been shut down years ago. No payment data, no card details, no merchant funds were touched.
Here is the part that matters. Checkout dot com refused to pay and then donated the same amount as the ransom demand to cybercrime research at Oxford and Carnegie Mellon. They admitted the mistake, fixed the legacy system, and redirected the money into something that helps everyone.
The awareness angle is simple, criminals rely on easy payouts. Every time someone refuses to pay, the business model weakens. And when a company can own an error and still come out with more trust, that is something worth celebrating.
∠The Awareness Angle
- Refusing to pay disrupts attackers - every rejected ransom makes cybercrime less profitable,
- Admitting the mistake builds trust - transparency always lands better than silence.
- Donating the ransom funds progress - the money now supports research that strengthens defences for everyone.
North Korean attackers turn Google’s Find Hub into a remote wipe tool
A North Korean group has worked out how to weaponise Google’s own Find Hub feature. They used phishing emails to steal Google account credentials, logged in, tracked victims, and then remotely wiped their Android devices. The worst part is that they timed the resets for when the person was physically away, so alerts were missed and recovery took longer. At the same time, the group hijacked trusted contacts on KakaoTalk and used those accounts to send malware disguised as stress relief apps. It is a clever mix of cloud account takeover and social trust.
∠The Awareness Angle
- Cloud accounts are now critical infrastructure - if someone gets into your Google or Apple account, they can do more damage than if they stole the device itself.
-
Messages from trusted contacts are not always safe - account hijacking makes malware look friendly, so unexpected files always need a second look.
-
Built in features can be misused - this attack relied on legitimate tools, not zero days, which means everyone needs to review how their own devices handle remote actions.
The first AI orchestrated cyber espionage campaign
A Chinese state linked group ran what appears to be the first large scale cyber espionage campaign driven almost entirely by an AI agent. They jailbroke Claude Code, fed it structured tasks, and used it to infiltrate around thirty organisations. Claude handled roughly eighty to ninety percent of the operation by itself. It scanned networks, wrote exploits, harvested credentials, exfiltrated the data, and even documented the work. Only a few human decisions were needed.
This is a real shift. It shows what happens when attacks operate at machine speed, with machine volume, and almost no human workload. OpenAI has strengthened detection and shared the case to warn people that this is now possible.
∠The Awareness Angle
- AI lets attackers scale attacks instantly - this campaign shows that intrusions can now run continuously and automatically without a big human team.
-
Guardrail bypassing is becoming a normal tactic - the group did not hack Claude, they persuaded it with careful prompts, which is exactly what employees could face too.
-
Defenders need automation to keep up - if attackers use AI to speed up reconnaissance and exploitation, security teams will need AI powered detection to match the pace.
Do you have something you would like us to talk about? Are you struggling to solve a problem, or have you had an awesome success? Reply to this email telling us your story, and we might cover it in the next episode!
Awareness Awareness
CIISec Live is coming up and it is all about behaviour and culture

CIISec Live takes place on the 25th of November at Heathrow and it looks like a brilliant day for anyone working in awareness or human risk. There are workshops on behaviour change, panel debates on what actually works, and sessions shaped by the audience rather than the stage. I will be on a panel that blends QI energy with a Who Wants to Be a Millionaire style format, all focused on one question. How do we really change behaviour and culture in cyber?
If your work touches training, engagement or behaviour, this is worth your time.
https://www.ciisec.live/
Think and Share, a brilliant awareness push for a good cause

There is a great initiative doing the rounds right now, supported by OutThink and started by Flavius. The idea is simple, share a short cyber safety tip, tag a few others, and each video raises money for cyber safety education in schools. It is a rare mix of awareness, community and impact.
Anna’s video deserves a special mention. She uses deepfake tools, timing and a smart creative build up to show how easily someone can fall for a convincing message. It is one of the best examples this week of turning a simple idea into something memorable. It shows what happens when you mix creativity with a security message, and it is exactly the kind of content that cuts through.
If your team or wider business is looking for something fresh to share, this challenge is worth supporting, and the videos make great conversation starters.
Watch Anna's video here
My chat with Dan from GoldPhish

I joined Dan from GoldPhish for a really fun conversation about keeping security simple, honest and human. We talked about why so much training feels overdone, why people switch off, and why small moments of clarity land better than perfectly polished content. Dan has a very real, no nonsense approach that lines up with how I see awareness, so this one felt natural from the first minute.
If you want something easy to listen to with a few proper laughs, give it a go.
Watch the chat - https://youtu.be/m5GNnSDepmQ
This Week's Discussion Points...
Breach Watch
Doctor Alliance healthcare breach exposes 1.24 million medical records – TechRadar
Watch | Read
Synnovis ends investigation into NHS ransomware attack linked to patient death – The Register
Watch | Read
DoorDash employee falls for social engineering attack, user data exposed – BleepingComputer
Watch | Read
Checkout dot com refuses ransom and donates equivalent to cybercrime research – Checkout dot com
Watch | Read
Two billion credentials indexed on Have I Been Pwned via Synthient dataset – HIBP
Watch | Read
The News
Ofcom found monitoring VPN usage with undisclosed third party tool – TechRadar
Watch | Read
Chinese built buses in Norway can be remotely halted by manufacturer – Euronews
Watch | Read
North Korean hackers misuse Google Find Hub to wipe Android devices – CSO Online
Watch | Read
AI orchestrated espionage campaign powered by jailbroken Claude Code – Anthropic
Watch | Read
Scotland launches cyber observatory to protect public services – UK Defence Journal
Watch | Read
New UK Cyber Security and Resilience Bill introduced to Parliament – ISP Review
Watch | Read
Quantum Route Redirect phishing as a service kit evades scanners – KnowBe4
Watch | Read
Awareness Awareness
CIISec Live 2025 at London Heathrow – CIISec
Watch | Read
Think and Share Challenge supporting cyber safety in schools – Anna Pieczatkowska
Watch | Read
Right Hand Cyber Halloween posters for awareness teams – Right Hand AI
Watch | Read
Jimmy Kimmel password on the street clip – YouTube
Watch | Read
Leanne Potter on how language shapes cyber and AI – LinkedIn
Watch | Read
Thanks for reading! If you’ve spotted something interesting in the world of cyber this week — a breach, a tool, or just something a bit weird — let us know at hello@riskycreative.com. We’re always learning, and your input helps shape future episodes.
And finally…A scammer who actually replied
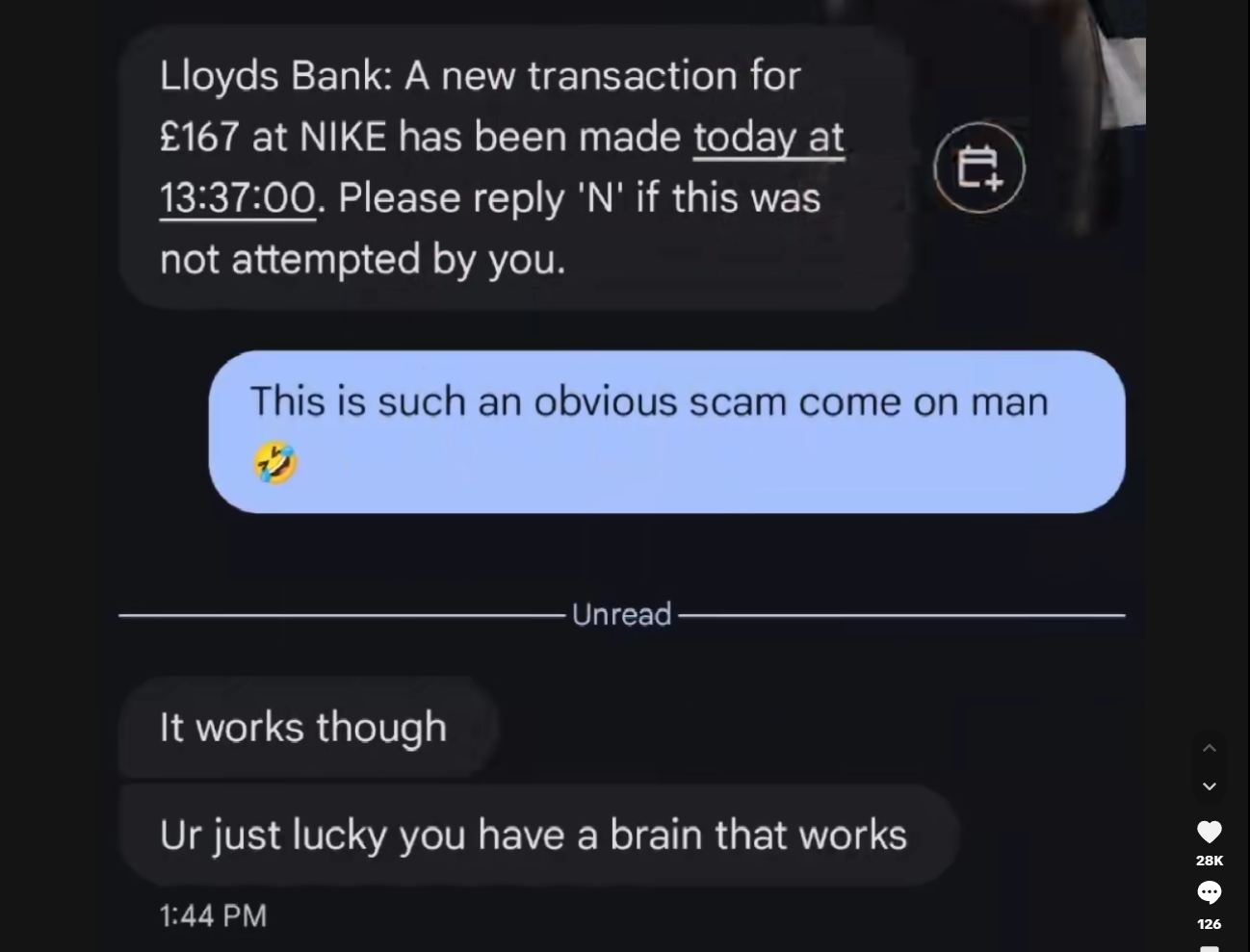
A text message pretending to be from Lloyds Bank made the rounds this week. The person who received it replied to say it was an obvious scam, and the scammer actually responded. That response showed there was a real person behind it, actively pushing and trying to get a reaction.
It is a reminder that these scams are not all harmless attempts or automated scripts. They are also run by people who know exactly how to pressure someone into acting quickly. For anyone who is older, isolated or less confident with technology, a message like this could easily feel genuine. It highlights why clear guidance, calm advice and simple steps are essential for anyone who might not recognise the signs straight away.
∠The Awareness Angle
- Real people run these scams - the scammer replying shows there is intent, pressure and manipulation behind the messages, which makes them more convincing for people who already feel stressed or unsure.
- Vulnerable people are the easiest targets - anyone who is older, isolated or less confident with tech is far more likely to reply without thinking, which is exactly what these scammers rely on.
-
Confidence is a defence in itself - knowing what a scam looks like helps you pause and check, so encouraging simple checks can make a big difference for those who feel less secure online.